Coronavirus Signs Fight the Coronavirus pandemic with effective visual reminders to practice safety in your offices, schools and facilities! Code Red is a worm that exploits a security hole in Microsoft Internet Information Server (IIS) to spread When it infects a server it startsThe Code Red worm first attacks the computer for 19 days It takes advantage of the security flaw in Microsoft software to deface sites The worm also helps attackers and helps them get control of the computer This was the only damage done to computers with this virus in them but the attackers could allow online vandals to make a lost of all

Red Gear Ring With Malware Bug A Computer Virus On World Map On Binary Code Background Vector Illustration Security Technology Concept Royalty Free Cliparts Vectors And Stock Illustration Image
Symbol code red virus
Symbol code red virus- Any link to or advocacy of virus, spyware, malware, or phishing sites A simple solution would be to insert the symbols and format with the red colour and the size you use most Then select and save as formatted autocorrect entries for #c (clubs) #h (hearts) etc Type #h to insert a red heart symbol Any other inappropriate content or The red spikes, also called spike proteins or S proteins, are what allow the virus to attack to human cells These clumps of proteins help the virus enter the body and bind to




Digital Skull And Crossbones On Binary Stock Vector Colourbox
A virus is only a virus if it can spread to other users You will need to figure out the delivery method before beginning, as it is one of the fundamentals of the virus's code Common delivery mechanisms include Executable file (EXE, BAT, COM etc) Code Red and Code Red II are both "worms," which are attacks that propagate themselves through networks without any user intervention or interaction Both take advantage of a flaw in a component of versions 40 and 50 of Microsoft'sAlert Level Icons Volcano updates include both a Volcano Alert Level and an Aviation Color Code In most cases, the alert level and aviationspecific color code will move together (eg, Normal and Green;
Sasser & Netsky are actually two separate worms, but they're often grouped together because the similarities in the code led experts to believe they were created by the same person Sasser spread through infected computers by scanning random IP addresses and instructing them to download the virus Netsky was the more familiar emailbased worm You might not even recognize that your computer is infected To help you out, here are five signs you can look for Popup ads Running into popupRedeem your ingame Fortnite rewards here!
Designs and Symbols 1 The waved pattern represents the perseverance and continuity of humankind to push forward with force and overcome obstacles like a powerful wave 2 The dove is for hope for those suffering illness from the virus or treatment 3 The angel is in honor of those who fought hard yet lost their life to the virus Code Red spread by taking advantage of a "hole," or weakness in the security system, of Microsofts IIS Estimates by Netcraft, an Internet consultancy based in Bath, England (http//netcraftcomCode Red is a worm that exploits a security hole in Microsoft Internet Information Server (IIS) to spread When it infects a server it starts to scan for other vulnerable servers and infects them During a certain period of time the worm only spreads, then it initiates a DenialofService (DoS) attack against www1whitehousegov and finally suspends all the activities



Banner Virus Protection Shield Icon On Background With Binary Code Stock Photo Alamy



What Is Virus Code Red How To Remove Like
If your computer suddenly starts taking forever to turn on or open up applications, that could be a symptom of malware infection, especially a worm or a Trojan horse, warns Sophie Miles, CEO andMany institutions use colors (eg "Code Red", "Code Blue") to identify specific types of emergencies "Code Red" and "Code Blue" are both terms that are often used to refer to a cardiopulmonary arrest, but other types of emergencies (for example bomb threats, terrorist activity, child abductions, or mass casualties) may be given "CodeVirus symbol images 595,5 virus symbol stock photos, vectors, and illustrations are available royaltyfree See virus symbol stock video clips of 5,959 sparkling water symbol database dot bacteria outline atoms logo bacteria good sparkling water




Code Red Virus



Bug Code Hack Internet Mobile Bug Seo Virus Icon Download On Iconfinder
Resistor Color Code Band 1 Band 2 Band 322 ohm R22 Red Red Silver27 ohm R27 Red Purple Silver33 ohm R33 Orange Orange Silver39 ohm R39 Orange White Silver47 ohm R47 Yellow Purple Silver Notation Tolerance56 ohm R56 Green Blue Silver68 ohm R68 Blue Gray Silver ohm R Gray Red Silver 10 ohm 1R0 Brown Black Gold 11 ohm 1R1 Brown BrownThe hexadecimal version of the therefore symbol (∴) would be ∴Scroll on for dingbats, circled numbers, script letter HTML codes, the angstrom sign, biohazard sign, alef symbol, HTML checkmark entity and even a heavy black heart And take a minute to browse Toptal's professional designers' blog, which gives you the lowdown on the very latest design trends and news—along with indepth tutorials and




Abstract Technology Pattern Red Symbol Virus Stock Illustration




Binary Code Infected With Virus High Resolution Stock Photography And Images Alamy
If you don't see the proper symbol files, the first thing to do is to check the symbol path dbgcmd 0000> sympath Current Symbol Path is d\MyInstallation\i386\symbols\retail If your symbol path is wrong, fix it If you are using the kernel debugger make sure your local %WINDIR% is not on your symbol pathCODE RED'S effects The creator of the code red virus is unknown, as the creator was never caught CODE RED Code red is not easy to remove which is quite annoying as it never does anything serious to your computer, but it can be removed by a specialist Who created CODE RED?



How To Protect Office 365 From Coronavirus Themed Threats Cso Online




Abstract Technology Pattern Red Symbol Virus Stock Vector Royalty Free
In most scenarios, the debugger automatically finds symbol files for user code, but if you want to step into (or debug) NET code, system code, or thirdparty library code, extra steps are required to obtain the correct symbol files You can load symbol information directly from the Modules window by rightclicking and choosing Load SymbolsHazard pictograms (symbols) Hazard pictograms alert us to the presence of a hazardous chemical The pictograms help us to know that the chemicals we are using might cause harm to people or the environment The GB CLP hazard pictograms appear in the shape of a diamond with a distinctive red border and white background This virus Formats the C ,D , and E Drive in 3 Seconds This is a very useful script if you want to learn how to create a virus using notepad No 10 Just open the Notepad and type the paste the following Code set ws=createobject("wscriptshell") dim strDir,strfile,st,strtxt2,strshell,strlog dim obfso,obfolder,obshell,obfile,obtxtfile



How To Make A Code Red Virus Youtube




The Code Red Worm Years On What Have We Learned Naked Security
The Department of Health on Saturday raised its alert system for coronavirus disease 19 (COVID19) to "Code Red" after it confirmed the first case of localized transmission of the deadly infection GMANETWORKCOM USES COOKIES TO ENSURE YOU GET THE BEST EXPERIENCE WHILE BROWSING THE SITEWUHAN, China (AP) — Since the coronavirus outbreak, life in China is ruled by a green symbol on a smartphone screen Green is the "health code" that says a user is symptomfree and it's required to board a subway, check into a hotel or just enter Wuhan, the central city of 11 million people where the pandemic began in DecemberA delightful reference for HTML Symbols, Entities and ASCII Character Codes HTML Arrows is a comprehensive reference website for finding HTML symbol codes and entities, ASCII characters and Unicode hexadecimal values to use in your web design Browse in grid or table format, search for HTML symbols, and check out Toptal's professional




Virus Germ Symbol Free Vector Graphic On Pixabay



The Top 10 Computer Viruses
Download this free picture about Virus Symbols Hazard from 's vast library of public domain images and videosNote that the hexadecimal numbers include x as part of the code Top of PageThe CodeRED Mobile Alert app enables subscribers to receive these notifications directly to their personal cell phone whether at home, on the road, or traveling around the country Alerts are initiated by authorized public safety officials to deliver locationbased notifications and are not issued by OnSolve or its staff Free alerts available*




Red Skull Virus On Green Binary Computer Code Background Stock Photo Picture And Royalty Free Image Image




Bug Emails Email Malware Spam Threat Virus Blue And Red D Bug Code Communication Png And Vector With Transparent Background For Free Download
Code Red was a computer worm observed on the Internet on It attacked computers running Microsoft's IIS web server It was the first large scale, mixed threat attack to successfully target enterprise networks The Code Red worm was first discovered and researched by eEye Digital Security employees Marc Maiffret and Ryan Permeh when it exploited a vulnerability discovered by Riley Hassell They named it "Code Red" because Mountain Dew Code RedThe Unicode numeric entity codes can be expressed as either decimal numbers or hexadecimal numbers For instance, the decimal version of the therefore symbol (∴) would be ∴Viruses When Trojan horses can propagate freely and insert a copy of itself into another file, it becomes a computer virus Def A computer virus is a program that inserts itself into one or more files and then performs some action The first phase is called the insertion phase where the virus inserts itself into a file The second phase is called the execution phase where the virus performs



1




Virus Bug In Program Code Stock Photo By C Pixeldreams
Enter your reward code to receive your Fortnite item Synopsis List of awareness ribbon colors and associated causes regarding health and disability Includes printable awareness ribbon chartAwareness ribbons are defined as short pieces of colored ribbon folded into a loop, or representations of such Awareness ribbons are used to create public awareness to health conditions and other important issuesFind vacation rentals, cabins, beach houses, unique homes and experiences around the world all made possible by hosts on Airbnb




Virus Text On Random Binary Code Red Screen Computer Technology Words Series 3d Render Stock Photo Picture And Royalty Free Image Image




Premium Vector Malware Ransomware Virus Encrypted Files And Show Key Padlock
Protect your mobile life with Android and iOS security These days much of your digital life is lived on your iPhone or Android phone McAfee ® Mobile Security provides malware and web protection and device security that helps you stay safe, particularly onthegoOur signs ship quickly and work effortlessly!Sensing an emergency, Sunil issued a ' Code Red,' a message announced over a hospital's public address system (PAS), indicating a fire or other adverse conditions that can cause grave problems




Surfing Dangerous Internet Environment Blue Padlock Icon On Red And Blue Binary Bit Code Background Data Security In Hacker Prone Crime Network Protection Against Virus Wall Mural Suebsiri




5 035 Computer Virus Photos And Premium High Res Pictures Getty Images
Last Saturday afternoon I received the official word that the Philippines has declared "CodeRed" which is the highest alert level that we can attain However we Code Red virus traced to China This article is more than 19 years old Sarah Left Fri 1045 EDT Officials in the US say they have traced the Code Red computer worm,Code Red Code Red was a computer worm observed on the Internet on It attacked computers running Microsoft's IIS web server The Code Red worm was first discovered and researched by two eEye Digital Security employees when it exploited a vulnerability




Code Red Computer Worm Wikipedia




Winter Covid 19 Collage Euro Mail And Rubber Zip Code Red Round Stamp Imitation Collage Euro Mail Is Formed Of Covid 19 Fir Tree And Frost Symbols Red Zip Code Seal Uses Circles
At Yahoo Finance, you get free stock quotes, uptodate news, portfolio management resources, international market data, social interaction and mortgage ratesAn X mark (also known as a cross, crossmark, x, or ex) is used to indicate the concept of negation (for example "no, this has not been verified", "no, that is not the correct answer" or "no, I don't agree") as well as an indicator (for example in election ballot papers or in x marks the spot)Its opposite is often considered to be the check mark or tick (or the O mark used in Japan, Korea• Use one of the many precautionary signages to ensure workplace safety and protocols for the Coronavirus (COVID19/nCoV) outbreak




The Easiest Way To Create A Fake And Harmless Virus Wikihow




Binary Blue The Word Red Virus Computer Virus Concept Binary Code Background Stock Illustration Illustration Of Background Monitor
Category page View source History Talk (0) The characters within Databrawl Characters within the Dataverse have three alignments they could potentially have Friendly This character has no intent to harm the computer, only to help it They most likely live here Unknown This character doesn't seem to want to harm or help the computer A virus or malware always has a negative impact, but the degree of that impact depends on the type and scope of the infection Here are some of the possible consequences of a computer infectionWarning and Red) However, there may be occasions when the hazards to groundbased communities and



Coronavirus Safety Tips Precautions Red Cross




Malware Ransomware Virus Encrypted Files And Show Key Lock With World Map On Binary Code And Gear Background Vector Illustration Cybercrime And Cyber Security Concept Stock Vector Image By C Nicescene
The wicarorg website was designed to test the correct operation of your antivirus / antimalware software The name "WICAR" is derived from the industry standard EICAR antivirus test file, which is a nondangerous file that all antivirus products flag as a real virus and quarantine or act upon as suchIf you know the gene symbol and species, enter them as follows tpo sym AND human orgn Click on the desired gene Click on Reference Sequences in the Table of Contents at the upper right of the gene record The NCBI Reference Sequences section of the record has links to NCBI curated records for transcripts (NM and XM prefix reference CODE RED Philippines' coronavirus cases rise to 6, DOH confirms local transmission




Pin On Computer Tips



Bug As A Symbol Of Malware And A Trojan Virus In The Program Code Hacking And Theft Of Personal Information And Data Blue Pixel Locks And Red Bug On A Black Background




Massive Botnet Could Take Down The Internet Researchers Warn




Computer Virus And Binary Code 3d Illustration Canstock



Shutterstock Puzzlepix




The Easiest Way To Create A Fake And Harmless Virus Wikihow



Bug As A Symbol Of Malware And A Trojan Virus In The Program Code Hacking And Theft Of Personal Information And Data Blue Pixel Locks And Red Bug On A Black Background
/what-to-do-when-you-see-a-virus-warning-popup-on-android-4768509-1-ae6d06dd24a248d29152ca67959989f6.png)



What To Do When You See A Virus Warning Pop Up On Android




Red Gear Ring With Malware Bug A Computer Virus On World Map On Binary Code Background Vector Illustration Security Technology Concept Royalty Free Cliparts Vectors And Stock Illustration Image




Red Binary Code Background Computer Problems Concept Black Background Malware Virus Data Transfer Stock Photo Picture And Royalty Free Image Image




3d Illustration Virus Dna Molecule Structure Concept Destroyed Code Human Genome Damage Dna Molecule Helix Consisting Particle Dots Dna Destruction Due To Gene Mutation Or Experiment Poster Id




Red Of Ring And Gears With Malware Bug A Computer Virus Inside On Binary Code Background Vector Illustration Security Technology Concept Royalty Free Cliparts Vectors And Stock Illustration Image




Malware Hazard Symbol Red Free Svg




Computer Virus And Binary Code Stock Photo By C Vladru




Technology Internet Data Security Protection Computer Privacy Secure Digital Web Protect Concept Access Information Business Network Safety Password Lock Cyber System Padlock Safe Hacker Background Code Crime Virus Software




Digital Skull And Crossbones On Binary Stock Vector Colourbox



Code Red Virus



23 384 Virus Code Photos Free Royalty Free Stock Photos From Dreamstime




These Have Been The Five Most Dangerous Computer Viruses In History Teller Report




Computer Virus Binary Code Wire With Red Viruses Stock Photo Download Image Now Istock




3d Covid 19 Corona Virus Shape Icon Structure Citypng



Collage Binary Tree Icon With Coronavirus Textured Code Red Stamp Stock Vector Illustration Of Grunge Combined



Coronavirus Collage Balloon Icon With Grunge Code Red Stamp Coronavirus Collage Balloon Icon And Round Corroded Stamp Seal Canstock




Corona Virus Protect You And Your Family Crowdcast



Computer Virus Images Search Images On Everypixel




What Is Malware How It Works What It Does Avg




The Difference Between A Virus Worm And Trojan Horse Digicert



Codered The Virus Encyclopedia




Bug As A Symbol Of Malware And A Trojan Virus In The Program Code Hacking And Theft Of Personal Information And Data Green Pixel Locks And Red Bug On A Black Background
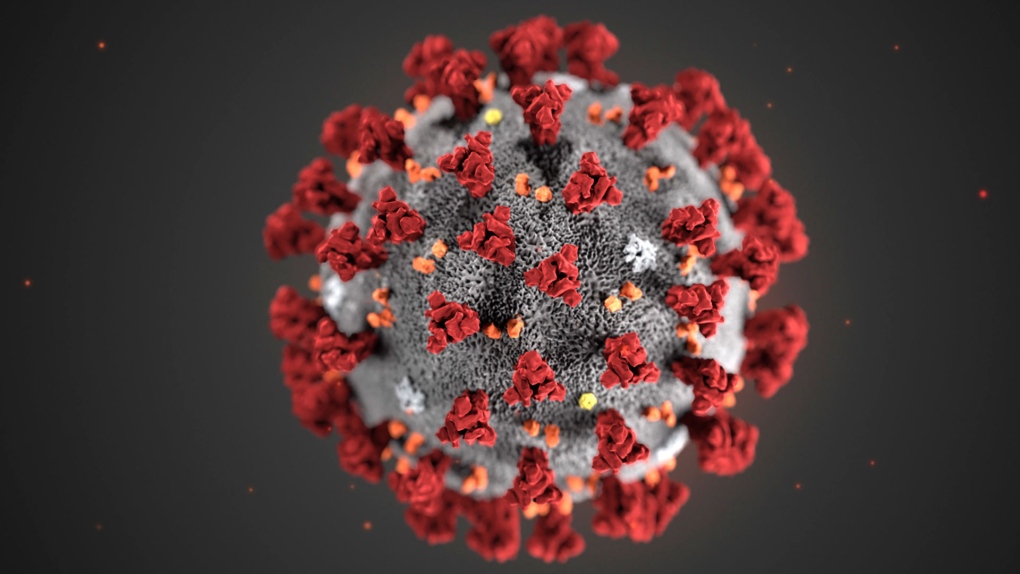



What Does Covid 19 Look Like A Closer Look At The Grey And Red Image That Symbolizes A Pandemic Ctv News



Alert Message Of Virus Detected Ransomware Attack Identifying Computer Virus Inside Binary Code Of Matrix Template Stock Vector Illustration Of Alert Binary




Virus Bug Code Skull Design Vector Art At Vecteezy



Code Red Computer Virus By Katie Aranda




Premium Vector Computer Virus Conceptual Idea




Bug As A Symbol Of Malware And A Trojan Virus In The Program Code Hacking And Theft Of Personal Information And Data Green Pixel Locks And Red Bug On A Black Background




Virus Germ Corona Free Vector Graphic On Pixabay




Analyzing The Financial Risk Of Ransomware With Fair




Concept Computer Virus Binary Code Red Stock Photo Edit Now



Virus Pc Icon Royalty Free Vector Image Vectorstock



Cyber Threat List Of Latest Computer Viruses 21




Code Red Computer Worm Wikipedia




Do You Know About Strange I Love You Virus Procaffenation




What Is Iloveyou Virus How To Prevent Iloveyou Virus Download



1




Coronavirus Mysteries That Still Can T Be Explained Reader S Digest



Code Red Virus Stock Photo Alamy



1



Malware Computer Virus Cyber Attack Icon Vector Image




Bug As A Symbol Of Malware And A Trojan Virus In The Program Code Hacking And Theft Of Personal Information And Data Red Pixel Locks And Green Bug On A Black Background




Code Red Virus




That Malware With Its Own Backdoor Into Android S Framework Don T Worry Google S On It Gulp Computerworld




School Infections Quarantines Reflect Uptick In Virus Spread News Spiritofjefferson Com




Red Skull Virus On Binary Computer Code License Download Or Print For 14 Photos Picfair




How To Beat Plague Inc Necroa Virus On Normal Levelskip




Bad Rabbit Ransomware Vector Photo Free Trial Bigstock




Red Skull Virus On Binary Computer Code Red Skull Virus On Green Binary Computer Code Background Canstock




Virus Line By Line Dangerous Stock Footage Video 100 Royalty Free Shutterstock




Tristar Red Sector Inc This Is The True Oldschool Hogback S Take On Our 30th Trsi Demoscene Anniversary In Ascii Ansi Petscii Style And Digitalart Design Symbol Code Crewlife




Malware 101 An Overview Of Malware Types Inc Com




Red Gear Ring With Malware Bug A Computer Virus On World Map On Binary Code Backgroundvector Illustration Security Technology Concept Stock Illustration Download Image Now Istock




Enraged Virus Pearl Steven Universe By 6the6overlord6 On Deviantart




Blue Padlock Symbol On Blue And Red Binary Code Bit Background Privacy And Data Security Concept




Stock Photos Royalty Free Images Vectors Footage Yayimages



1




Vector Stock Comuter Laptop With Malware Bug A Computer Virus On Red Binary Code Background Vector Illustration Security Technology Concept Clipart Illustration Gg Gograph




Abstract Technology Pattern Red Symbol Virus Stock Illustration




Computer Virus High Resolution Stock Photography And Images Alamy




Attack Of Code Red Virus Shipou




What Is Virus Code Red How To Remove Like




Code Red Archives Foreign Policy




5 039 Computer Virus Photos And Premium High Res Pictures Getty Images



Red Virus Warning Sign Biohazard Icon Symbol Vector Image




Corona Symbol Coronavirus Free Photo On Pixabay




You Ve Probably Seen This Image Of The Coronavirus Everywhere What Is It Exactly Poynter




Cool Red Black Chemical Biohazard Danger Symbol Classic Round Sticker Zazzle Com




Code Red Virus




Virus Hall Of Fame Code Red Fixmestick Startmestick Blog




What Is Virus Code Red How To Remove Like



0 件のコメント:
コメントを投稿